E-Financial Fraud - Smishing, Phishing, Pharming
With the recent rise in interest rates increasing household debt burdens, cases of electronic financial fraud have also been on the rise. For those unfamiliar with the various fraud tactics, here’s a brief summary of common terms (while you can easily search for this information, I’ve compiled it for your convenience)
Phishing
A combination of the words “Private Data” and “Fishing,” phishing is a fraud technique where personal information is "fished" to steal financial data and extort money. Tactics include using smishing (SMS phishing), phone calls, and messaging apps.
Smishing
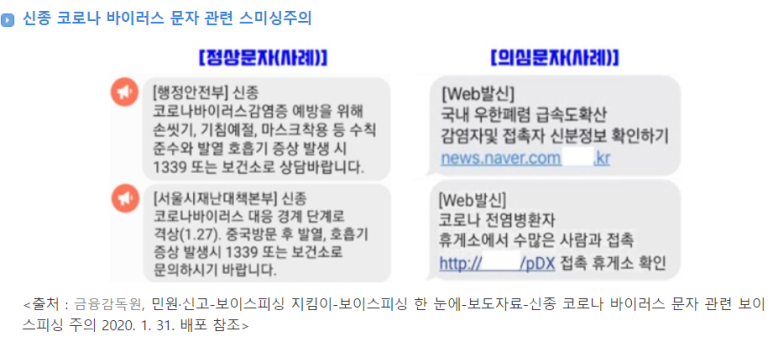
A type of phishing that targets users through SMS (text messages). While spam emails are often quickly deleted due to familiarity, text messages with familiar content like "free coupon offers," "first birthday invitations," or "wedding invitations" can trick people into clicking malicious links. Once clicked, personal information such as passwords or email accounts may be stolen, or a malicious app installer file may be downloaded onto the smartphone. If this file is executed, the harmful app will be installed.
Smishing Fraud Process
- Click on the internet link in the text message.
- Malicious code is installed on the smartphone.
- Without the victim’s knowledge, small payments are made, or personal/financial information is leaked.
Pharming
Another type of phishing, pharming is a large-scale technique that steals personal information through websites. It is a combination of "Phishing" and "Farming." Hackers infect legitimate websites with malware, manipulating the PCs of users who access these sites and stealing their financial data.
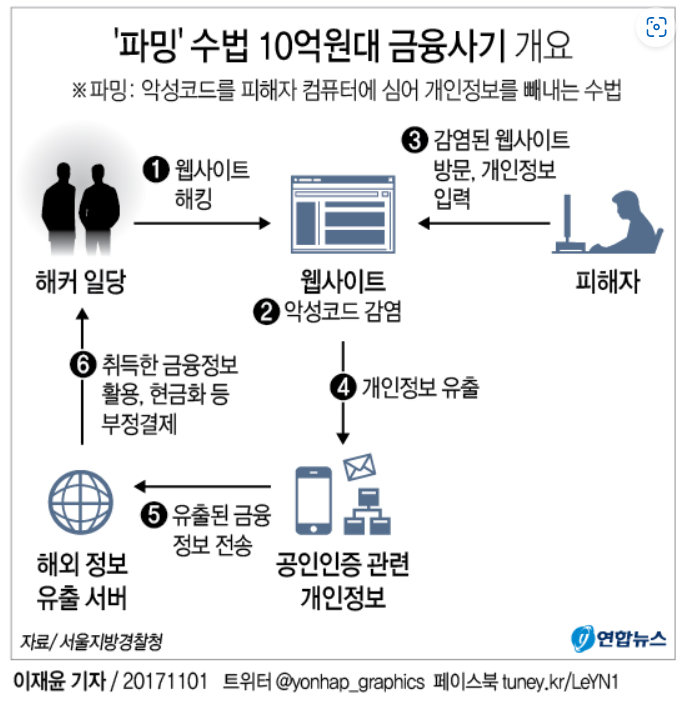
Pharming Process
- Even when users access a legitimate website, if their PC is infected with malware, they are redirected to a fake site.
- The fake site demands sensitive information such as entire security card numbers, stealing personal and financial details.
- Using the stolen information, the fraudsters make withdrawals, payments, or transfers.
Solutions
- Do not store certification files, security card photos, or passwords on your PC or in your email.
- Be suspicious and double-check any websites you don’t normally visit.
'IT' 카테고리의 다른 글
| IT System Preventive Maintenance (0) | 2022.12.13 |
|---|---|
| Multi-Factor Authentication (0) | 2022.11.05 |
| 구글 애드센스 승인 거절 - 사이트가 다운되었거나 사용할 수 없음 (0) | 2022.11.04 |
| Proxy Server (0) | 2022.10.31 |
| What is a WLC (Wireless LAN Controller)? (0) | 2022.10.30 |



